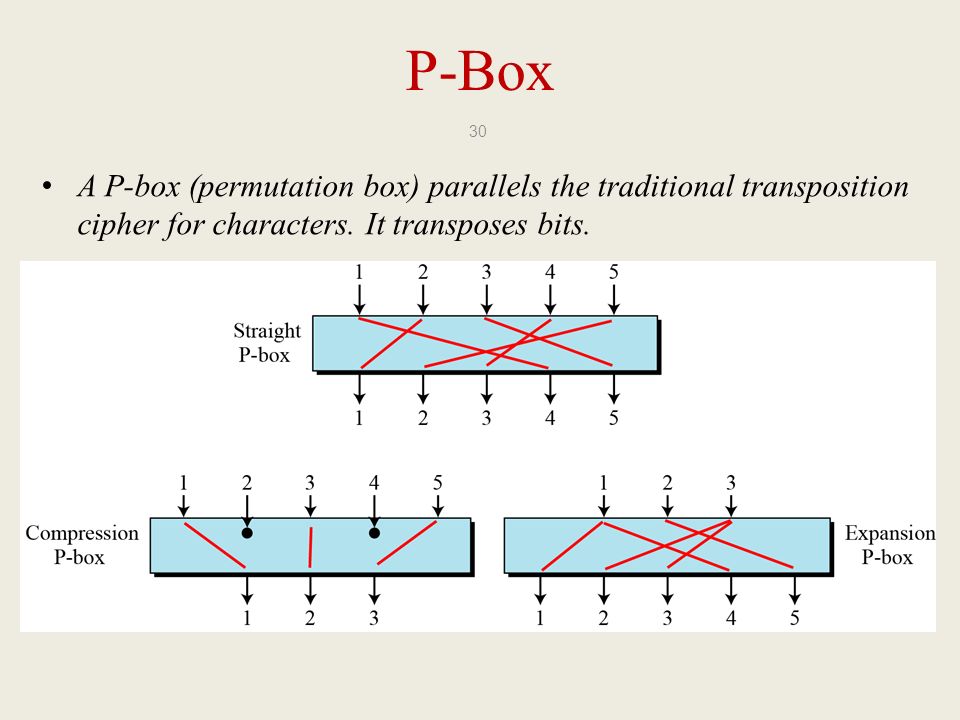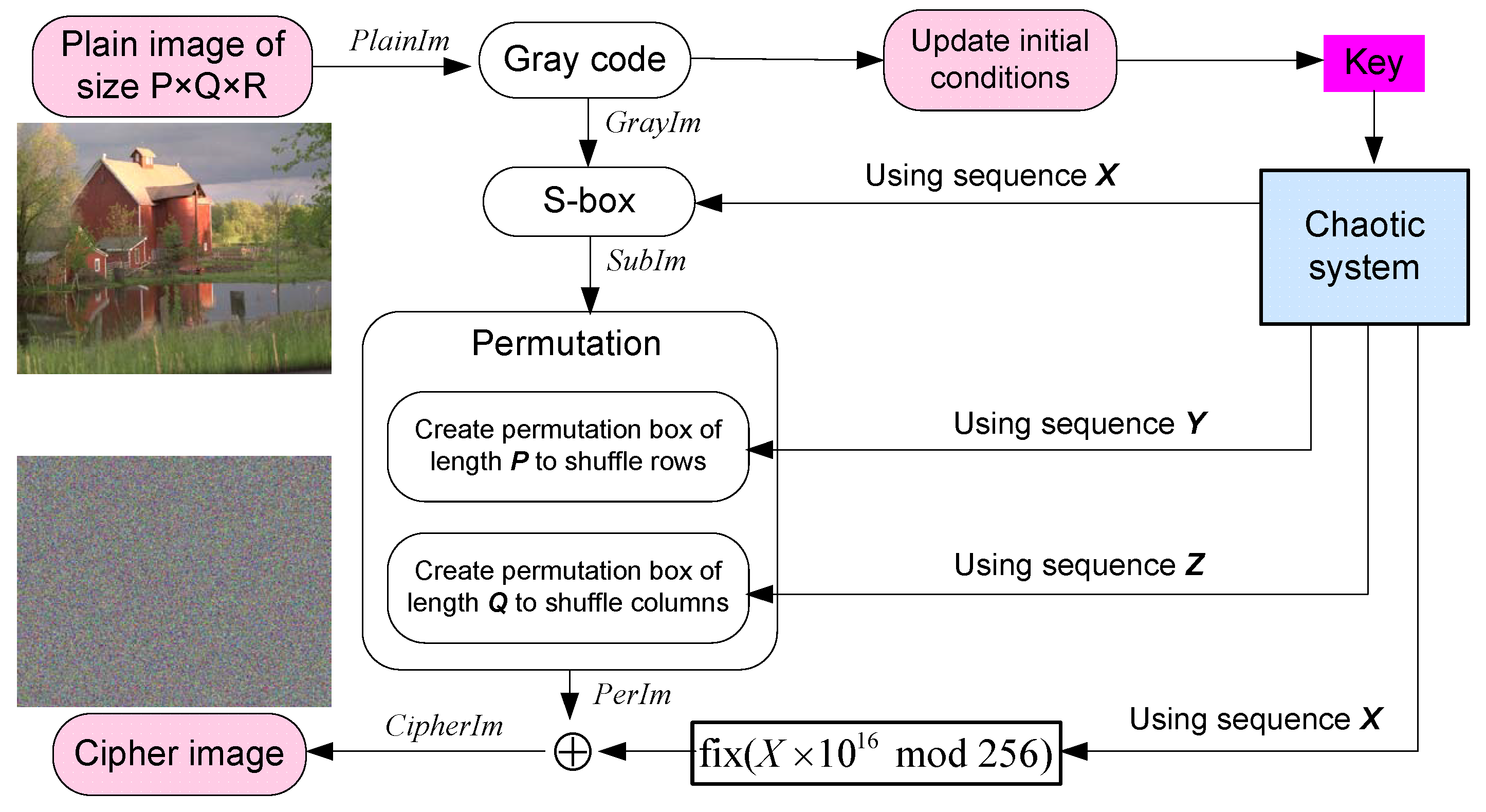
Electronics | Free Full-Text | Efficient Chaos-Based Substitution-Box and Its Application to Image Encryption | HTML
S-Box Design - Symmetric Ciphers and Hashes - Modern Cryptography: Applied Mathematics for Encryption and Informanion Security (2016)

An algorithm for the construction of substitution box for block ciphers based on projective general linear group: AIP Advances: Vol 7, No 3
![Mathematical recreations and essays. Mathematical recreations; Geometry; Bees; Cryptography; Ciphers; String figures; Magic squares. CH. XI] MISCELLANEOUS PROBLEMS 225 cell or small square empty; the puzzle is to move them so Mathematical recreations and essays. Mathematical recreations; Geometry; Bees; Cryptography; Ciphers; String figures; Magic squares. CH. XI] MISCELLANEOUS PROBLEMS 225 cell or small square empty; the puzzle is to move them so](https://c8.alamy.com/comp/RDXBXM/mathematical-recreations-and-essays-mathematical-recreations-geometry-bees-cryptography-ciphers-string-figures-magic-squares-ch-xi-miscellaneous-problems-225-cell-or-small-square-empty-the-puzzle-is-to-move-them-so-that-finally-they-occupy-the-position-shown-in-the-first-of-the-annexed-figures-d-top-of-box-ft-a-bottom-of-box-b-9-p-sjg-pi-w-we-may-represent-the-various-stages-in-the-game-by-sup-posing-that-the-blank-space-occupying-the-sixteenth-cell-is-moved-over-the-board-ending-finally-where-it-started-the-route-pursued-by-the-blank-space-may-consist-partly-of-tracks-fo-RDXBXM.jpg)
Mathematical recreations and essays. Mathematical recreations; Geometry; Bees; Cryptography; Ciphers; String figures; Magic squares. CH. XI] MISCELLANEOUS PROBLEMS 225 cell or small square empty; the puzzle is to move them so
![9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book] 9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book]](https://www.oreilly.com/library/view/computer-security-and/9780471947837/images/ch009-t007.jpg)
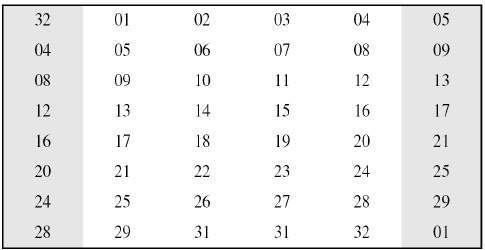
9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book]


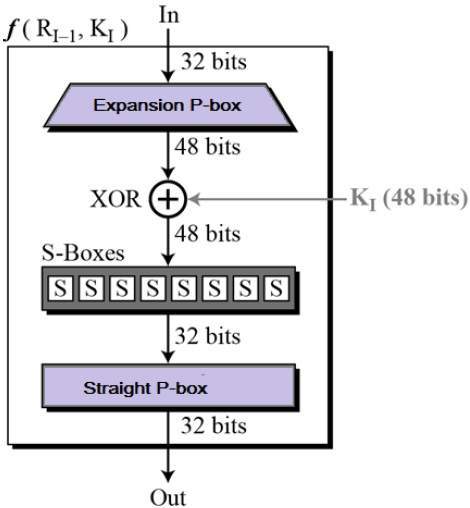
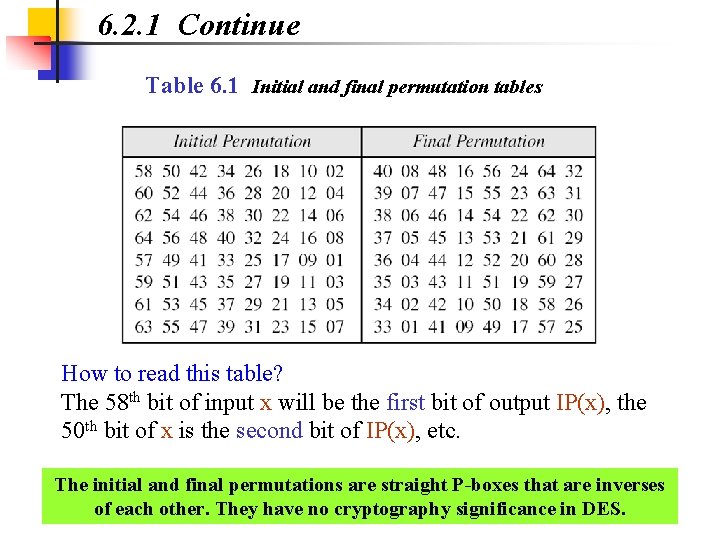

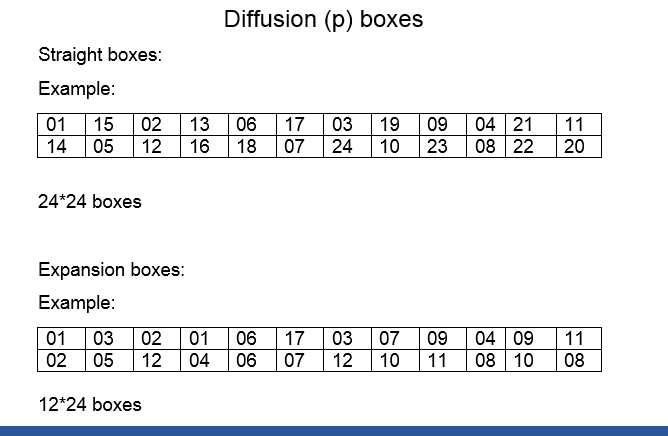
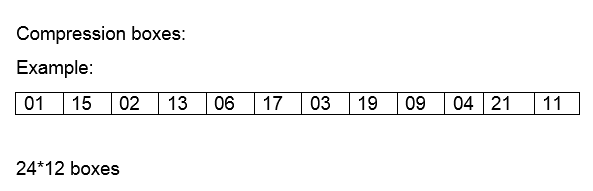

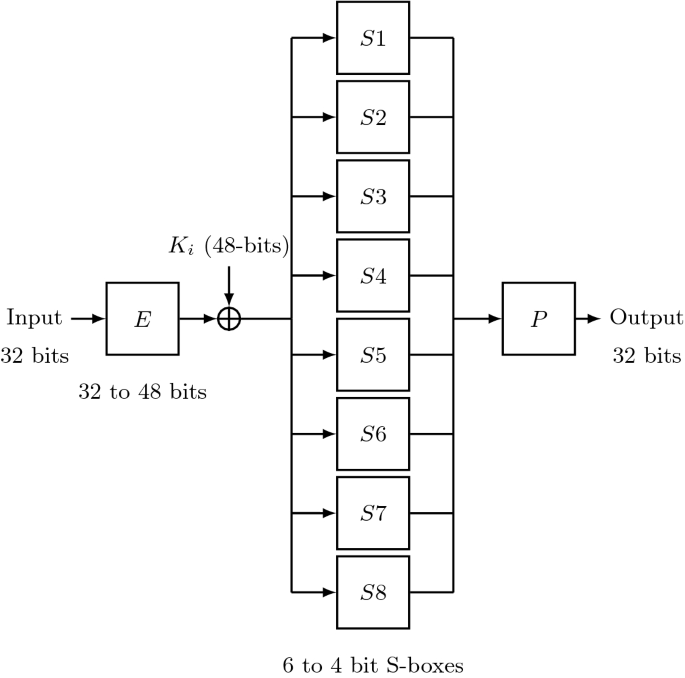
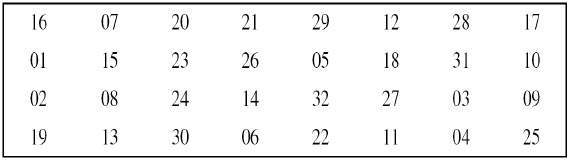
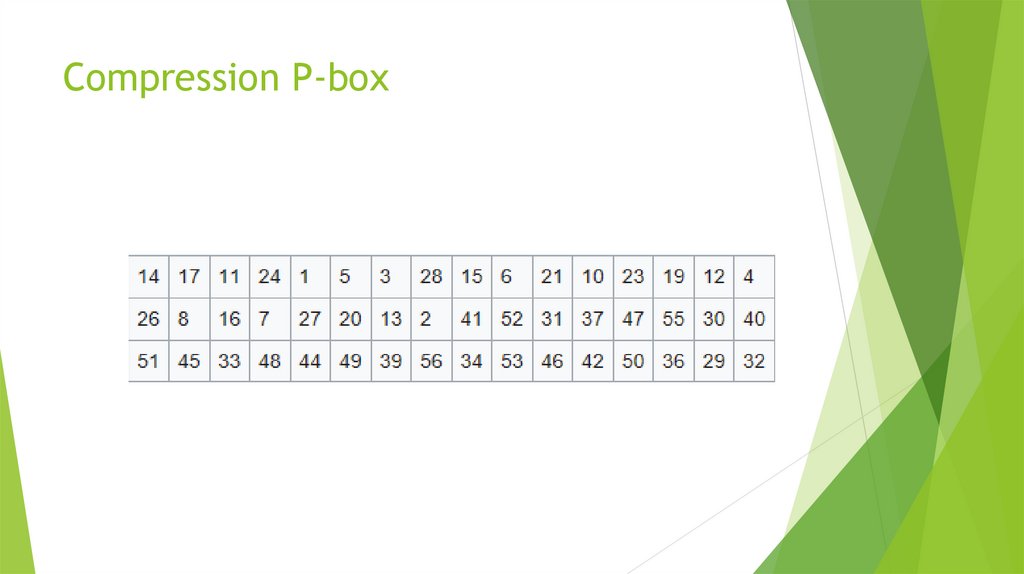


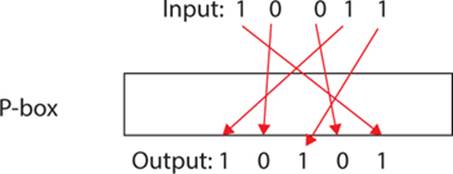
![Solved] A permutation block (P-box) in a modern block cipher is an example of | SolutionInn Solved] A permutation block (P-box) in a modern block cipher is an example of | SolutionInn](https://s3.amazonaws.com/si.question.images/images/question_images/1607/4/9/7/5845fd077702398f1607497583269.jpg)